Recently, we had an issue of some machines not backing up the Bitlocker recovery password to active directory, even with the GPO in place. They ended up being offline while the bitlocker process took place. Plus, some of the systems in AD had multiple entries, which can be cumbersome. To mitigate this issue, I have implemented an SCCM Configuration Baseline that makes sure the Bitlocker recovery password is backed up to AD and that it is the only recovery password present.
NOTE: This script is being used in an environment that only encrypts the %systemdrive%. If your environment encrypts other items such as flash drives, removable HDDs, and etc, you will need to modify these scripts to meet your environment needs. It will delete those items from active directory also.
To do this, I first implemented a baseline that enabled the RSAT active directory feature in Windows 10. This is needed so the scripts can query and write to AD. Once this was deployed, I created the BitLocker Recovery Password Backup configuration item.
Platforms must be set to Windows 10 as some of the cmdlets used in the scripts only exist in that OS and newer.
The script returns a true or false value that dictates if remediation is needed.
The first script queries the local system and AD for the recovery passwords to compare. If they match and only one is in AD, then True is returned that dictates the system is in compliance. False is returned if there is no password stored in AD, there is more than one password in AD, or the wrong password is stored in AD.
Here is the discovery script:
NOTE: This script is being used in an environment that only encrypts the %systemdrive%. If your environment encrypts other items such as flash drives, removable HDDs, and etc, you will need to modify these scripts to meet your environment needs. It will delete those items from active directory also.
To do this, I first implemented a baseline that enabled the RSAT active directory feature in Windows 10. This is needed so the scripts can query and write to AD. Once this was deployed, I created the BitLocker Recovery Password Backup configuration item.
Platforms must be set to Windows 10 as some of the cmdlets used in the scripts only exist in that OS and newer.
The script returns a true or false value that dictates if remediation is needed.
The first script queries the local system and AD for the recovery passwords to compare. If they match and only one is in AD, then True is returned that dictates the system is in compliance. False is returned if there is no password stored in AD, there is more than one password in AD, or the wrong password is stored in AD.
Here is the discovery script:
$RecoveryKey = (Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | Where-Object {$_.KeyProtectorType -eq 'RecoveryPassword'}
$ADBitLockerRecoveryKey = (Get-ADObject -Filter {objectclass -eq 'msFVE-RecoveryInformation'} -SearchBase (Get-ADComputer -Identity $env:COMPUTERNAME).DistinguishedName -Properties 'msFVE-RecoveryPassword')
If ($ADBitLockerRecoveryKey -eq $null) {
Echo $false
} elseif ($ADBitLockerRecoveryKey -isnot [system.Array]) {
If (([string]$RecoveryKey.RecoveryPassword).Trim() -eq ([string]$ADBitLockerRecoveryKey.'msFVE-RecoveryPassword').Trim()) {
Echo $true
} else {
Echo $false
}
} elseif ($ADBitLockerRecoveryKey -is [system.Array]) {
Echo $false
}
Next comes the remediation script. This is what will be executed if the discovery script returns a False value:
$RecoveryKey = (Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | Where-Object {$_.KeyProtectorType -eq 'RecoveryPassword'}
Write-Host 'Local Recovery Password:'$RecoveryKey.RecoveryPassword
$ADBitLockerRecoveryKey = (Get-ADObject -Filter {objectclass -eq 'msFVE-RecoveryInformation'} -SearchBase (Get-ADComputer -Identity $env:COMPUTERNAME).DistinguishedName -Properties 'msFVE-RecoveryPassword')
Write-Host ' AD Recovery Password:'$ADBitLockerRecoveryKey.'msFVE-RecoveryPassword'
If (($ADBitLockerRecoveryKey -isnot [system.Array]) -and ($ADBitLockerRecoveryKey -ne $null)) {
Remove-ADObject -Identity $ADBitLockerRecoveryKey.DistinguishedName -Confirm:$false
} elseif ($ADBitLockerRecoveryKey -is [system.Array]) {
Foreach ($Key in $ADBitLockerRecoveryKey) {
Write-Host 'Removing'$Key.DistinguishedName
Remove-ADObject -Identity $Key.DistinguishedName -Confirm:$false
}
}
Backup-BitLockerKeyProtector -MountPoint $env:SystemDrive -KeyProtectorId $RecoveryKey.KeyProtectorId
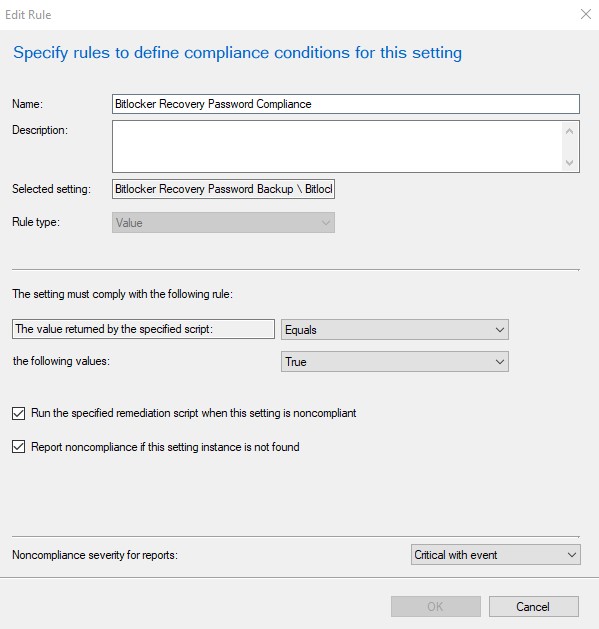
The final thing to set in the configuration item is the compliance rule as shown below:
Now that the configuration item is created, the configuration baseline must be created and deployed. Here are the screenshots of my configuration baseline that I later deployed out to all laptop systems, which are the systems here that are BitLockered.