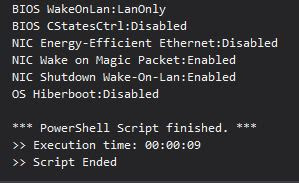
If you have a system that has been infected or the drive had to be replaced, you'll need to lay down a new bare OS and then have autopilot finish up the configuration of the machine. For this, we are using MDT as it is easy to maintain and very fast at imaging.
I used this as a template to come up with the solution we are now using. The first thing I did was to use everything verbatim from the section of the blog named "How to get the Windows Autopilot payload". It is the next section How to customize the MDT Task Sequence for Autopilot that I diverged from. I could not get that section to work. The main problem was the task sequence. The blog says to use a custom task sequence when in reality, you must use a Standard Client Task Sequence.
The first thing I did was to disable Postinstall and State Restore groups as we will not be joining a domain and the task sequence needs to stop in Postinstall mode. The next thing was to create a new Postinstall group as shown below.
The next thing was to create the CustomSettings_Autopilot.ini as described in the referring blog. The Gather uses the CustomSettings_Autopilot.ini file as described in the blog.
The Apply Autopilot Profile also uses what is described in the other blog.
- xcopy %SCRIPTROOT%\AutopilotConfigurationFile.json %OSDisk%\Windows\provisioning\AutoPilot\ /c
The next stip is to delete the unattend.xml file as shown below:
The next task places a file named autopilot.txt in the root directory of the c: drive. This is a flag to run the Intune package that will delete all MDT associated files and registry keys to terminate the MDT build.
The next task will delete most of the MDT files on the system.
Finally, the Restart task reboots the system at which point it will come up to the Autopilot user signon page.
As far as the SetupCompleteAutopilot.cmd file, here is what I have inside it. I changed some of the script to use environmental variables and I added the deletion of the c:\autopilot.txt file and the creation of the same file under c:\windows\temp to signify the script executed and the system has been cleaned up so the Intune package registers the execution as a success.
@echo off
:: // ***************************************************************************
:: //
:: //
:: // File: SetupComplete.cmd
:: //
:: // Version: 1.0
:: //
:: // Purpose: Cleanup after MDT Autopilot deployment
:: //
:: // ***************************************************************************
:: Copy to windows setup folder for application verification purposes in Intune
copy /V /Y \\prodfs01\All\ProdApps\Waller\SetupComplete\SetupCompleteAutopilot.cmd %WINDIR%\Setup\SetupCompleteAutopilot.cmd
:: Workaround for incorrectly-registered TS environment
reg delete HKCR\Microsoft.SMS.TSEnvironment /f > nul 2>&1
rmdir /Q /S %OSDisk%\MININT
rmdir /Q /S %OSDisk%\_SMSTaskSequence
del /Q %OSDisk%\LTIBootstrap.vbs
del /Q %OSDisk%\autopilot.txt
echo Test > %WINDIR%\Temp\autopilot.txt
In Intune, I created the app called MDT Cleanup. Here is the program page. I used a dummy delete.cmd file as that part is not needed.
That is all that is to the Intune package. Now the system will build a bare-bones OS and then transfer the rest of the build process to Intune.